Jackpotting = Free Cash!? Malware + Hackers
Malware called “Cutlet Maker” is designed to make ATM’s eject all of the money inside them according to a law enforcement official. Thi is called Jackpotting.
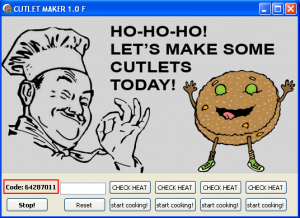
“Ho-ho-ho! Let’s make some cutlets today!”
Curlet Maker’s control panel reads the above. It shows cartoon images of a chef and a cheering piece of meat. This means in Russian, a cut of meat. However it also can bean a bundle of cash.
Jackpotting
A joint investigation between our friends over at Motherboard and the German broadcaster Bayerischer Rundfunk (BR) looking into “jackpotting”
A spate of attacks on ATM’s in Germany in 2017 saw thieves make off with more than 1M Euros.
Jackpotting is where cybercriminals use malware or hardware to trick ATM’s into ejecting all of the money inside of them. No need to use a credit card either. They’ll install the malware onto an ATM by prying open a panel and loading it on using a USB stick and USB port.
Although a European non profit said that Jackpotting attacks have decreased, multiple sources tell Motherboard that attacks in other parts of the world have gone up. Such as the US, Latin America and Southeast Asia. Impacting both the banks and ATM manufacturers.
“The U.S. is quite popular,” a source familiar with ATM attacks told Motherboard.
(Motherboard and BR granted multiple sources, including law enforcement officials, anonymity to speak more candidly about sensitive hacking incidents.)
Showing off…
During an annual Black Hat cybersecurity conference in 2010. Late researcher even demonstrated live on stage his own strain of ATM malware. His malware displayed JACKPOT on the ATM as it threw out the cash in a steady stream.
Christoph Hebbecker, a prosecuting attorney for the German state of North Rhine-Westphaila told Motherboard that his office is investigating 10 incidents between February and November 2017. Hackers stole 1.4M Euros, Hebbecker said. He continued that because of the similar nature of all the attacks. He believes that they could be linked to the same criminal gang.
Multiple sources told Motherboard that the attacks in 2017 impacted Santander; two sources said they specifically involved the Wincor 2000xe model of ATM, made by the ATM manufacturer Diebold Nixdorf.
A Santander spokesperson said in an emailed statement to Motherboard,
“Protecting our customers’ information and the integrity of our physical network is at the core of what we do. Our experts are involved at every stage of product development and operations to protect customers and the bank from fraud and cyber threats. This focus on protecting our data and operations prevents us from commenting on specific security issues.”
Furthermore, officials in Berlin, said they had seen at least 36 jackpotting cases since Spring 2018. With 1000’s of Euro’s stolen. Across Germany over the past several years 82 attacks have occured, according to police spokespeople. While not all of them were successful cash outs.
Aging ATM’s
ATM Jackpotting isn’t limited just to a single bank or ATM manufacturer. “You will see this across all vendors; this is not dedicated towards a specific machine, nor towards a specific brand, and definitely not a region,” Redecker said.
A reason for the security issue is that ATM’s, for many of them, are aged Windows computers.
“These are very old, slow machines,” the source familiar with ATM attacks informed Motherboard.
While many ATM manufacturers have made improvements to their devices, it doesn’t mean that all ATM’s will be up to the same standard, Redecker from Diebold Nixdorf stressed.
Furthermore responsibility on securing access to the ATM’s is the banks responsibility too.
“In order to execute a jackpotting attack, you have to have access to the internal components of the ATM. So, preventing that first physical attack on the ATM goes a long way toward preventing the jackpotting attack,” David N. Tente, executive director of USA, Canada & Americas at the ATM Industry Association (ATMIA), said in an email to Motherboard.
Cheap Software
“The bad guys are selling these developments [malware] to just anybody….That has enabled smaller outfits or enterprising criminals to start targeting ATMs..Potentially this can affect any country in the world,” David Sancho, senior threat researcher at cybersecurity firm Trend Micro, and who works with Europol on jackpotting research, said to Motherboard.
Motherboard spoke to one cybercriminal claiming to sell the Cutlet Maker malware.
“Yes I’m selling. It costs $1000,” they wrote in an email, adding that they can offer support on how to use the tool as well. The seller provided screenshots of an instruction manual in Russian and English, which steps potential users through how to empty an ATM. Sections of the manual include how to check how many banknotes are inside the ATM, and installing the malware itself.
The European Association for Secure Transactions (EAST), a non-profit that tracks financial fraud, said jackpotting attacks decreased 43 percent over the previous year, in a report published this month. But it’s worth stressing that EAST’s report only covers Europe.
“It happens in parts of the world where they don’t have to tell anybody about it,” the source familiar with ATM attacks added. “It’s increasing, but, again, the biggest problem we’ve got is that nobody wants to report this.”
Heading to the US?
“Globally, our 2019 survey indicates that jackpotting attacks are increasing,” Tente from ATMIA wrote in an email to Motherboard.
As the source familiar with ATM attacks said, “There are attacks happening, but a lot of the time it’s not publicized.”
(VICE)F
Keep up to date with everything How To Kill An Hour by signing up to our newsletter by clicking here!
Let us know what you think of the show by clicking here!
Click here to subscribe to our YouTube Channel to see more amazing ways to kill time!
Follow us on Twitch by clicking here!






